How Wazuh can help organizations with Regulatory Compliance
Regulatory compliance management is becoming more prominent for different types of enterprises year after year. Regulatory compliance refers to an organization’s conformance to relevant laws, regulations, guidelines, and specifications. When a business meets compliance frameworks with its internal security measures, it helps keep data safe and enforces the organization’s integrity and reputation. File integrity monitoring (FIM) is indicated as a requirement in several of the compliance objectives.
Following are some examples of security standards that indicate FIM functions as a requirement:
- Payment Card Industry Data Security Standard (PCI DSS)
- The Health Insurance Portability and Accountability Act of 1996 (HIPAA)
- Federal Information Security Management Act (FISMA)
- Sarbanes-Oxley Act (SOX)
- The General Data Protection Regulation 2016/679 (GDPR)
- The California Consumer Privacy Act (CCPA)
- The Dodd-Frank Act
Regulatory compliance processes and strategies guide organizations to ensure data protection. Consumers are placing more trust in enterprises that adhere to regulatory compliance rules that protect personal data while the number of security breaches continues to rise. In addition, when companies incur regulatory violations, this may result in legal repercussions, including federal fines.
Enterprises that do not adhere to specified regulatory compliance regulations may be forced to engage in remediation programs involving on-site compliance audits and inspections by the relevant regulatory agencies.
Organizations that don’t follow regulatory compliance processes can suffer financial penalties. Moreover, companies that have repeated compliance violations can potentially harm their brand’s reputation. Below, we will take a look at how Wazuh’s FIM module can help organizations meet regulatory compliance needs.
Introducing Wazuh
Wazuh is an industry-leading threat prevention, detection, and response platform that is free and open source. It secures on-premises workloads as well as virtualized, containerized, and cloud infrastructures. Currently, Wazuh is being adopted by hundreds of companies worldwide, ranging from small businesses to major corporations.
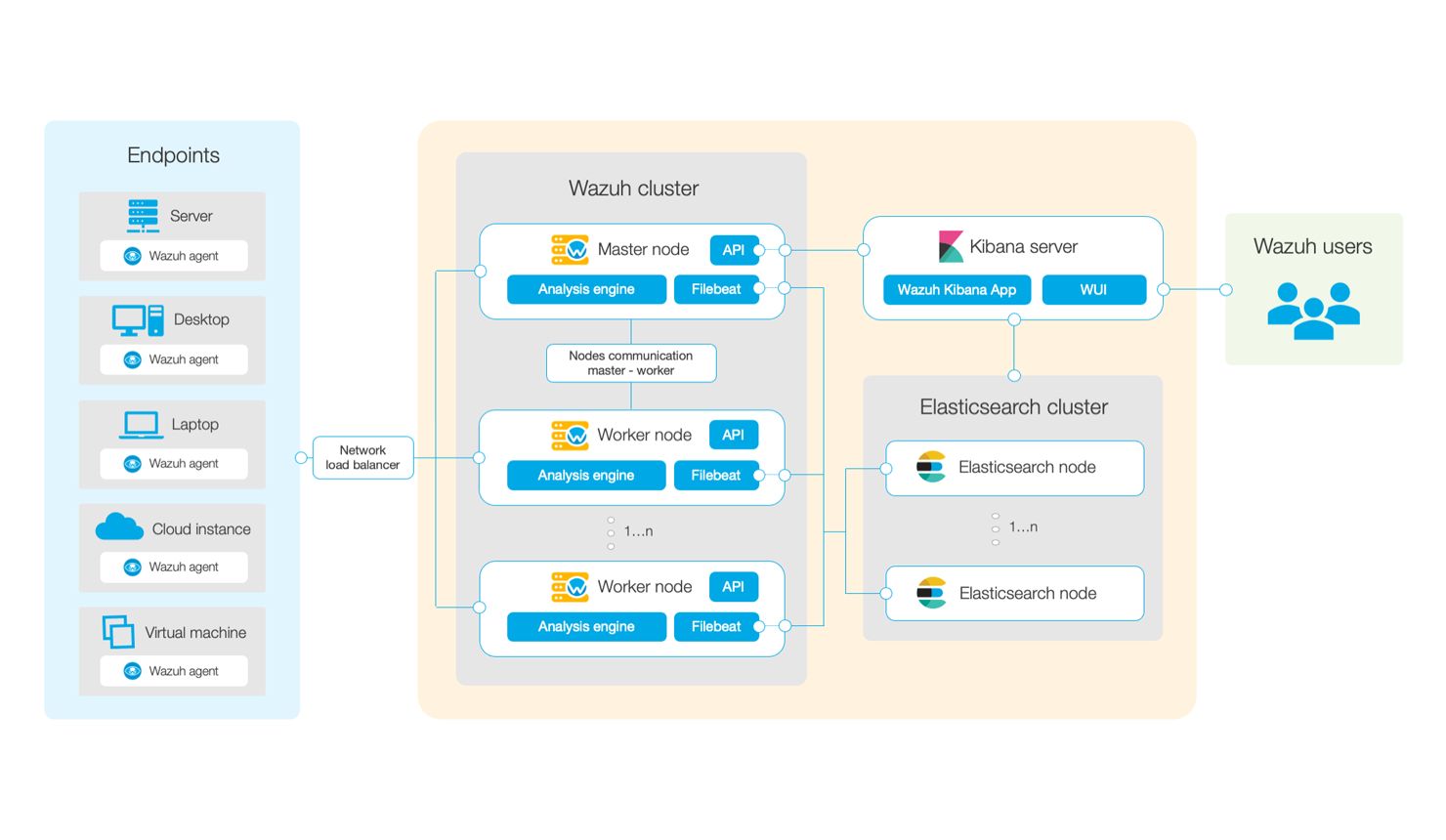
The Wazuh platform is a protection solution that consists of a collection of agents deployed in the monitored endpoints and one or several management servers that collects and analyses the data received from those agents. Wazuh has also been fully integrated with the Elastic Stack, allowing customers to acknowledge and manage security alerts using an intuitive search engine and data visualization tool.

Image – Wazuh Architecture (Source)
Wazuh agent transmits events to the central Wazuh server continually for analysis and threat detection. The Wazuh server then decodes and checks the received events using the analysis engine.
On the other hand, the Wazuh server sends alerts and event data to the Elasticsearch server using Filebeat, which uses TLS encryption. Filebeat reads the output data from the Wazuh server and transmits it to the Elasticsearch server. Kibana is then used to mine and show the data on the dashboard once it has been indexed by Elasticsearch.
Below is a list of the most significant Wazuh capabilities:
- File integrity monitoring
- Security analytics
- Intrusion detection
- Log data analysis
- Vulnerability detection
- Configuration assessment
- Incident response
- Regulatory compliance
- Cloud security
- Container’s security
How does FIM work?
The FIM module is included within the Wazuh agent that performs regular system scans and saves the cryptographic checksums and attributes of the monitored files to a database. This module looks for modifications by comparing the checksums against the baseline’s initial file information. Then the agent warns the Wazuh manager about the detected changes.
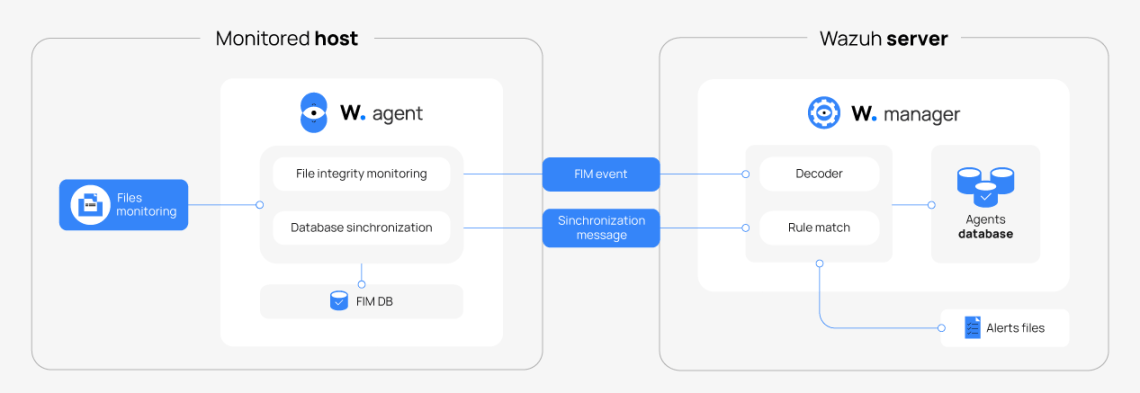
FIM monitoring is based on periodic integrity synchronization between the Wazuh agents and managers, updating only outdated data, and optimizing FIM data transmission. FIM can generate alerts when a change is detected according to the Wazuh agent configuration.
Some of the items that could be configured are:
- Files or directories that the user wants to be monitored
- The frequency of the Scheduled scans
- Real-time monitoring for the list of directories
- Who data monitoring for directories (that uses Linux Audit subsystem & Microsoft SACL)
- Reporting new files that are added to the system
- Windows registry monitoring for the list of registry entries that need to be monitored
- Reporting files and registries value changes
- The alert severity for the monitored files or directories
FIM – Dashboard


FIM – Integrity Monitoring

Summary
In summary, FIM is a critical component of regulatory compliance for organizations that require meeting specific requirements, designing processes to address these requirements, and accessing many industry-specific practices. Due to its ability to address regulatory compliance objectives, Wazuh is a well-positioned regulatory compliance solution.




Average Rating